2.1 Creating Required Roles
Overview
In this section, we will create the necessary IAM Roles for the AWS services used in this project. These roles will allow AWS services to access different resources within your AWS account.
The roles include:
- Role for Lambda to access S3
- Role for EC2 to access Kinesis
- Role for Lambda to access Kinesis and DynamoDB
- Role for Glue to access S3
Create a Role for Lambda to Access S3
- Go to the AWS Console and select IAM from the services menu.
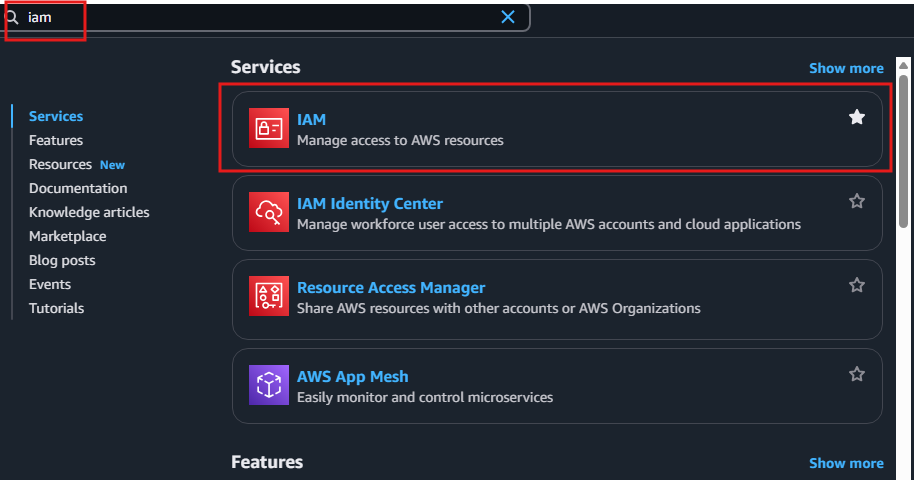
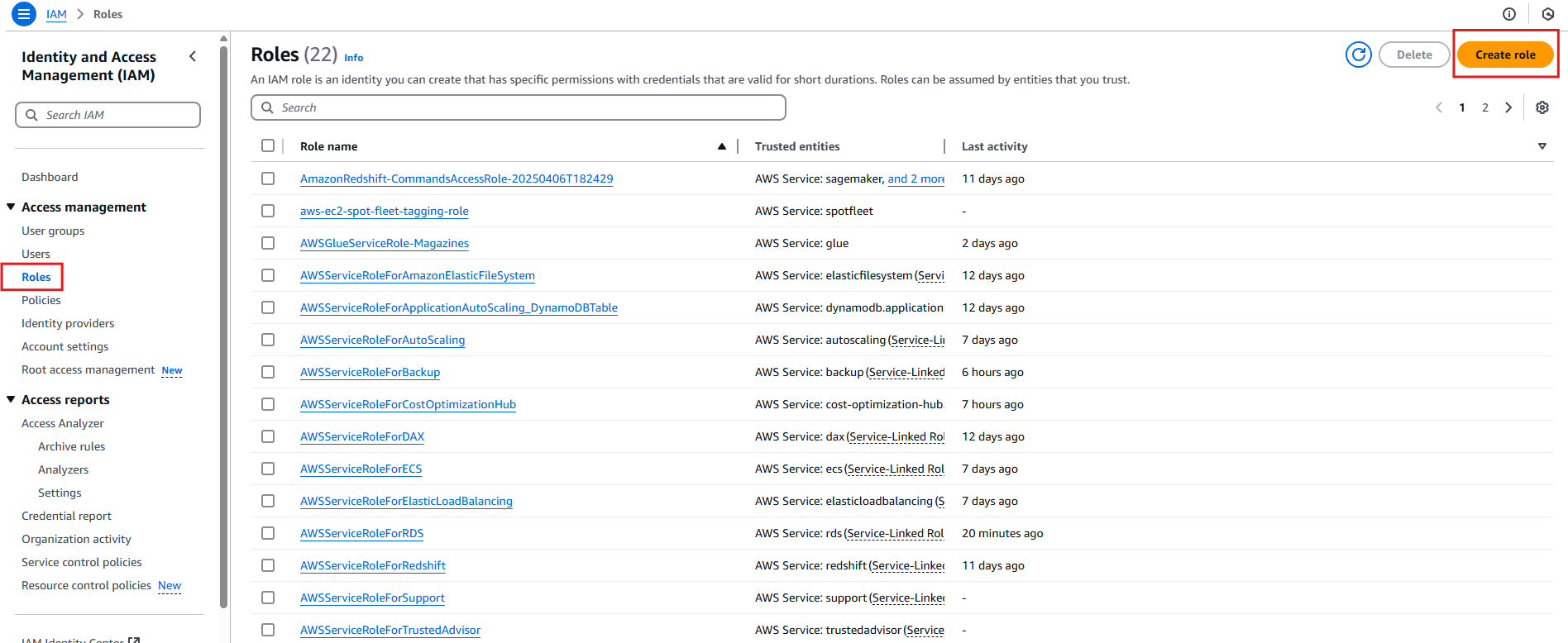
- Select Roles from the left menu, then click Create role.
- On the Select trusted entity screen, choose AWS service, then select Lambda from the list of services. Click Next.
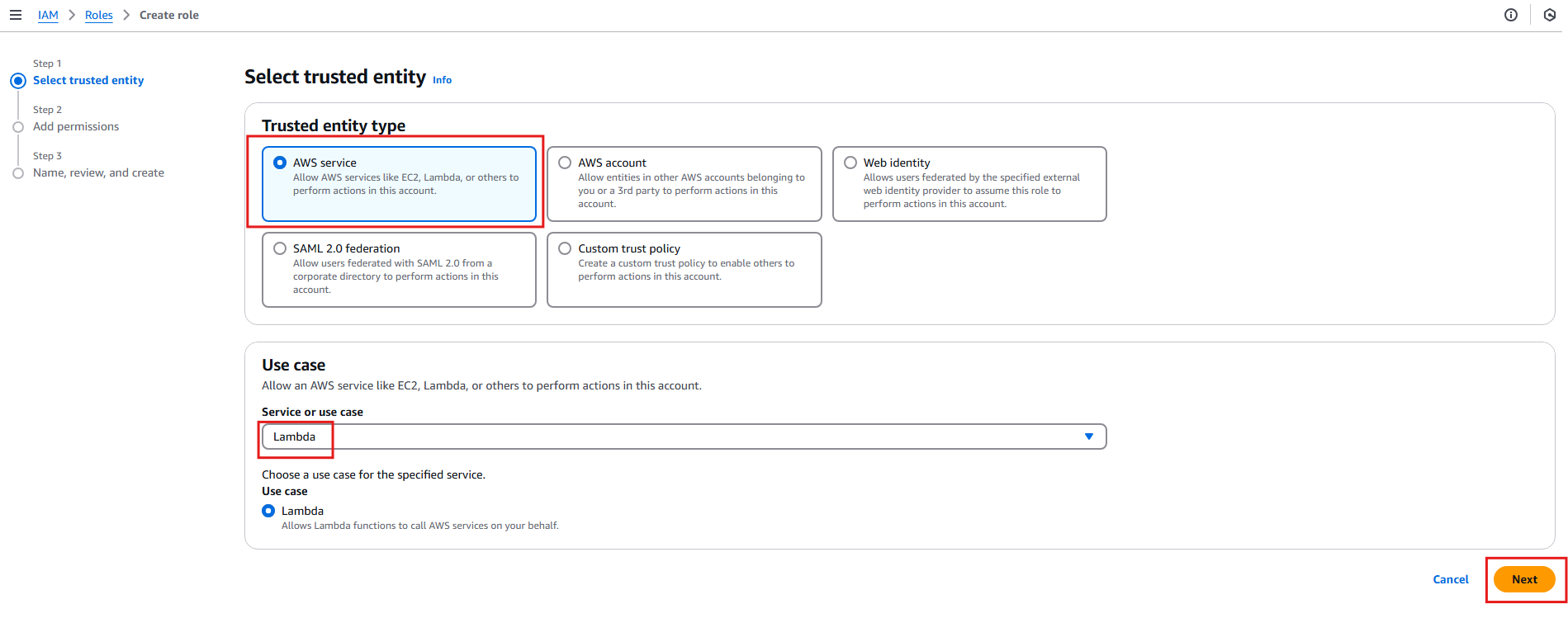
In the Add permissions section:
- Search for and select AmazonS3FullAccess from the policy list.
- Search for and select AWSLambdaENIManagementAccess from the policy list.
- Click Next.
In the Name, review, and create section:
- Enter the role name as
lambda-s3-full-access. - For the description, enter
Allow Lambda access S3 with Full Access. - Click Create role.
- Enter the role name as

Create a Role for EC2 to Access Kinesis
- Go to the AWS Console and select IAM from the services menu.

- Select Roles from the left menu, then click Create role.

- On the Select trusted entity screen, choose AWS service, then select EC2 from the list of services. Click Next.
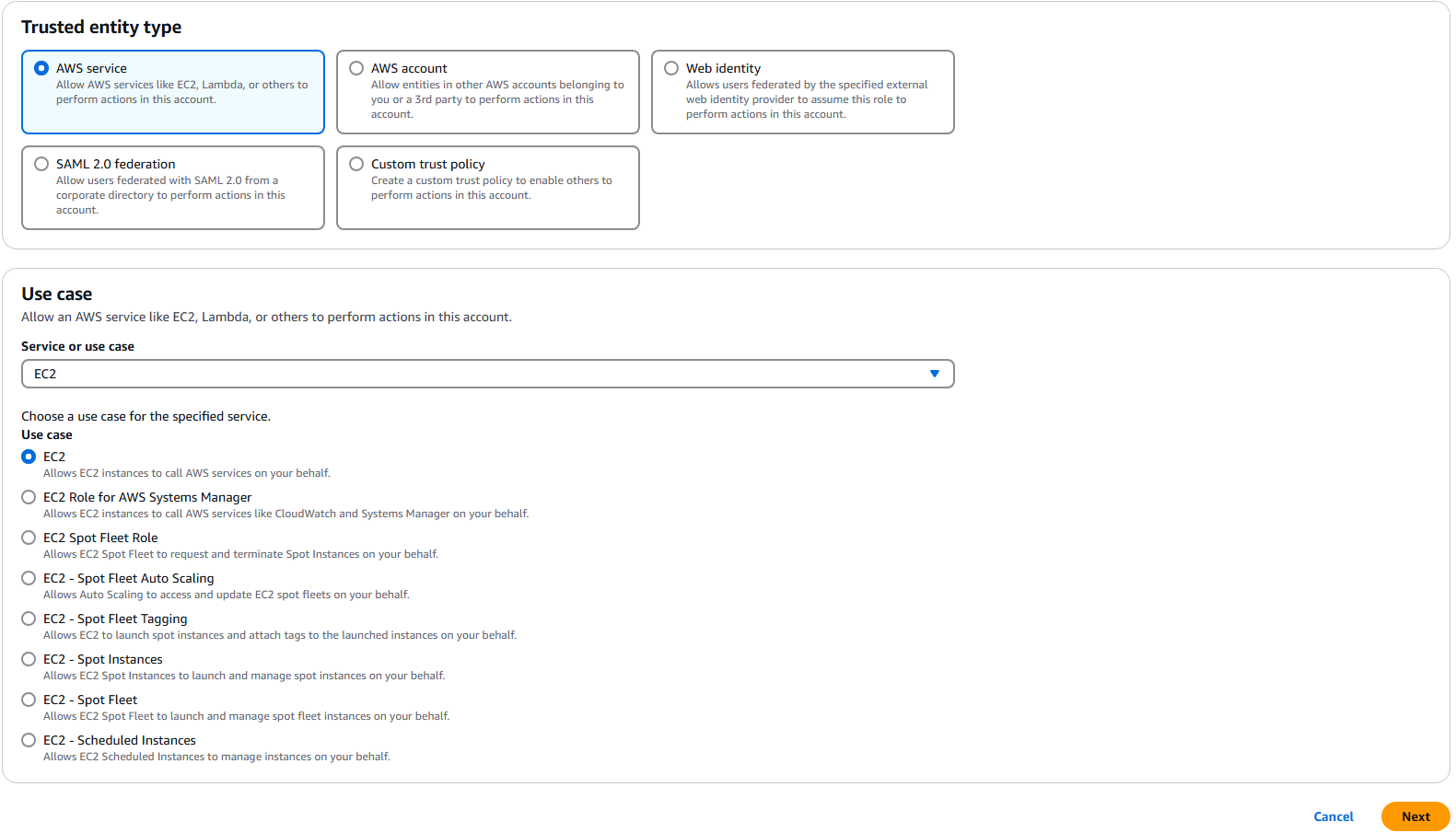
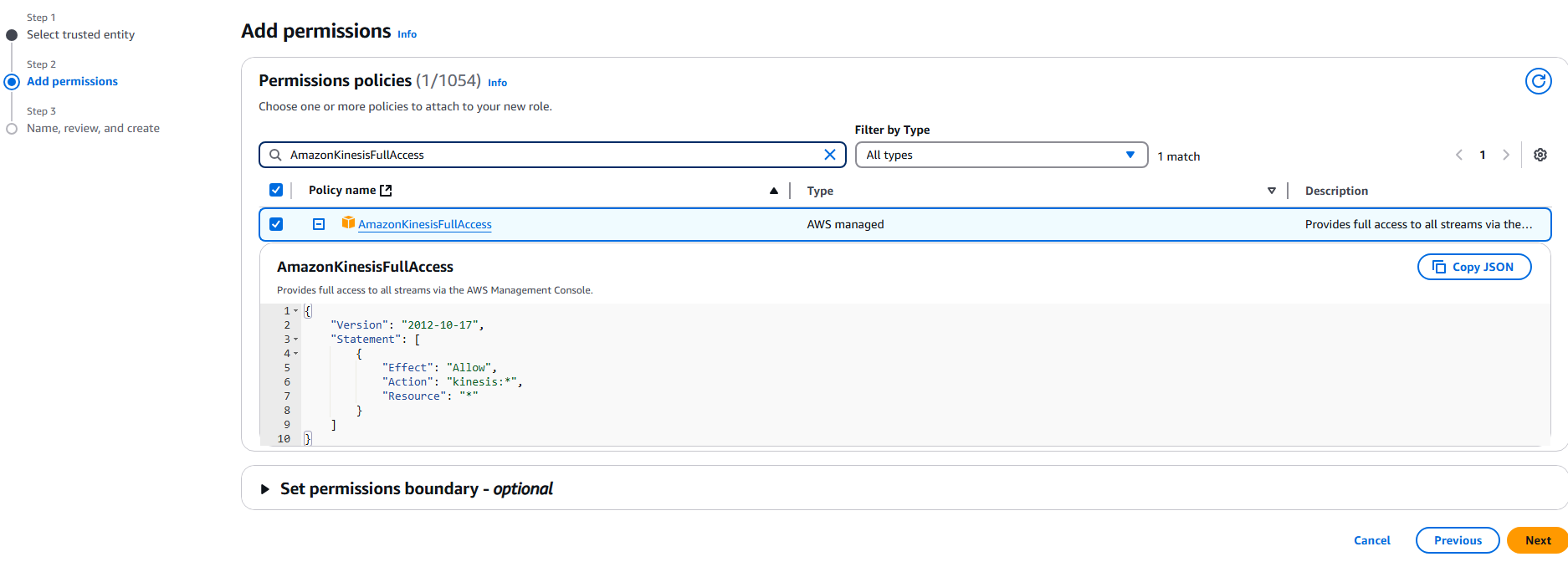
- In the Add permissions section:
- Search for and select AmazonKinesisFullAccess from the policy list.
- Click Next.
- In the Name, review, and create section:
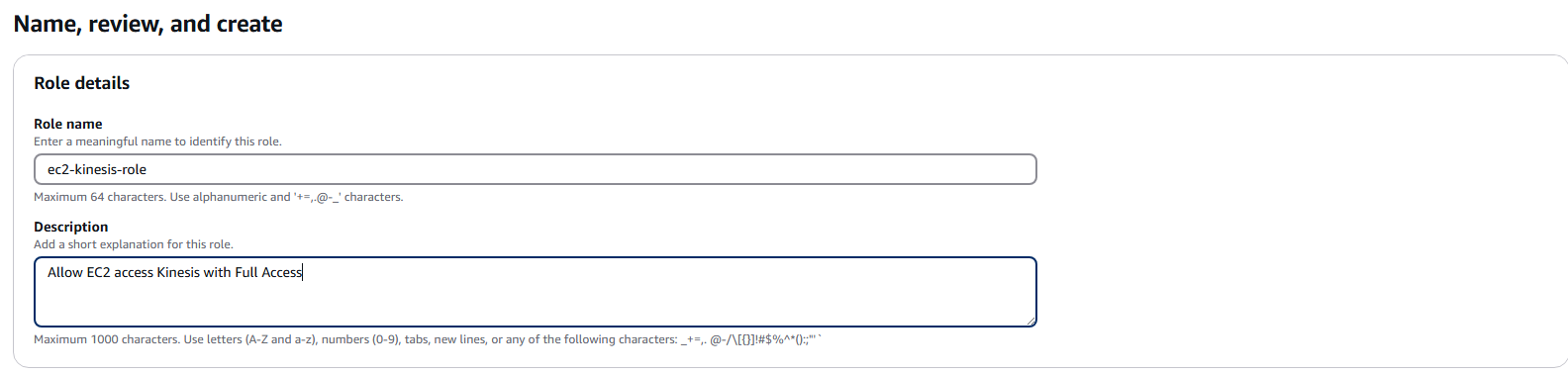
- Enter the role name as
ec2-kinesis-role. - For the description, enter
Allow EC2 access Kinesis with Full Access. - Click Create role.
- Enter the role name as
Create a Role for Lambda to Access Kinesis and DynamoDB
- Similar to the steps above, create a role with the use case as Lambda.
- In the Add permissions section:
- Search for and select AmazonKinesisFullAccess from the policy list.
- Search for and select AmazonDynamoDBFullAccess from the policy list.
- Search for and select AmazonAthenaFullAccess from the policy list.
- Search for and select AWSLambdaBasicExecutionRole from the policy list.
- Search for and select AmazonS3FullAccess from the policy list.
- Click Next.
- In the Name, review, and create section:
- Enter the role name as
lambda-kinesis-dynamodb-role. - For the description, enter
Allow Lambda access Kinesis and DynamoDB and S3 with Full Access. - Click Create role.
- Enter the role name as
Create a Role for Glue to Access S3
- Similar to the steps above, create a role with the use case as Glue.
- In the Add permissions section:
- Search for and select AmazonS3FullAccess from the policy list.
- Search for and select AWSGlueServiceRole from the policy list.
- Click Next.
- In the Name, review, and create section:
- Enter the role name as
AWS-Glue-S3-Full-Access. - For the description, enter
Allow Glue access to S3 with Full Access. - Click Create role.
- Enter the role name as